Safe Computing
The cybersecurity landscape is ever-changing. Every day there are new threats to New York Tech’s information assets, our personal information, and all digital information, both known and unknown. While the pandemic may have put the past year on pause for most of us, it did not for those who saw new opportunities to make us fall victim to cybercrime.
One of the methods where we've seen the largest increase in activity is phishing scams.
Phishing (pronounced: fishing) is an attack that attempts to steal your money, or your identity, by getting you to reveal personal information -- such as credit card numbers, bank information, or passwords -- on websites that pretend to be legitimate. Cybercriminals typically pretend to be reputable companies, friends, or acquaintances in a fake message, which contains a link to a phishing website.
Phishing is a type of attack where someone masquerading as a trusted entity tries to steal your login credentials, credit card numbers, or other important data. They may include an unsolicited link and ask you to provide credentials to reset a password or a bank account number to accept a payment. Any unverified source asking for information should raise a red flag.
A few of the more common phishing scams involve people/organizations (known in the security industry as “threat actors”) posing as employees of the Department of Labor, the IRS, or as medical personnel distributing the COVID-19 vaccine. The scams look something like this:
Department of Labor – you are contacted by someone who appears to be from the Department of Labor. An email may include a bank name in the subject line, state that you have received a payment, and then ask you to click on a link or open an attachment for directions on how to claim it. Or a phone call may ask you for personal information in order to process the payment.
IRS/Tax – a person claiming to be from the IRS or someone else involved with tax collection will contact you via email or phone call asking for personal information in order to process your tax return or refund. They may even go as far as to threaten to notify the authorities if you fail to provide the requested information.
COVID-19 Vaccine – threat actors will reach out to you via email or phone call to inform you that you've been selected for the vaccine based on family and/or medical history. They will then ask for personal information in order to sign you up for the vaccine.
**IMPORTANT**
- Do NOT provide any personal or payment information of any kind via email or over the phone until you can positively verify the party on the receiving end.
- For emails, check the “from” address. It may appear as a name, but checking the actual address may reveal it's fraudulent.
- You will NEVER be contacted directly by the IRS or other governmental agency and be asked to provide personal information.
In an effort to combat these attacks, the ITS team has already implemented a number of solutions, including Microsoft’s Advanced Threat Protection (ATP), which scans all links and attachments contained in incoming emails to ensure their safety. However, this may not stop all phishing emails. It is important to remain vigilant.
Knowledge and awareness are among the most important and effective tools in fighting cybercrime. ITS will continue to focus on educating the New York Tech community on how to identify scams and best protect themselves. You can find additional resources and information on our common phishing tactics and best practices web page.
Every one of us must do our part to keep our friend’s and colleague’s information safe and secure. For more information, or to report any suspicious activity, please contact the ITS Help Desk at nyit.edu/itshelp or call 516.686.1188.
Uptick in Phishing Emails Impersonating New York Institute of Technology Employees
Spring 2021
More
Over the past several months, ITS Help Desk has been notified by a number of faculty and staff members who have received messages from senders that are impersonating managers, deans, and supervisors – even the president. This is a practice known as “spoofing.” Different versions of these emails ask the recipient to:
- Quickly arrange for a gift card purchase for an athletic recruit, or prospective student, or to cover a university expense
- Make an immediate wire transfer to an unfamiliar account
- Pay an online invoice Typically in these Phishing e-mails, the FROM address shows the name of a New York Tech manager, department chair, or dean, along with an unfamiliar email address.
Sometimes the address itself is forged and looks like a real nyit.edu address. The SUBJECT may be a generic request for help (for example, "Quick Task,” “Are you available,” "Urgent request") or an invoice number. The body of the email may be something as simple as “Are you free? I’m heading into a meeting and cannot accept a phone call” or “Can you text me at xxx-xxx-xxxx” to something a little more descriptive such as “I need you to help me get iTunes gift cards from the store. I’ll reimburse you when I get back to the office.”
In all cases, the request is deemed as urgent and the intent is to make it appear that someone at New York Tech in a position of authority is directing you to complete a university or personal task via email. By responding, you risk theft, malware, and account compromise. Please use caution when reviewing these messages and never click on any links or attachments from unknown sources.
Fall 2019
More
As we make our way to the end of the fall semester and the holiday break, we would like to remind you to be diligent in watching for phishing emails. Over the past several weeks, ITS Help Desk has been notified by a number of faculty and staff members who have received messages from senders that are impersonating managers, deans, athletic director/coaches, and supervisors – even the president. This is a practice known as “spoofing.” Different versions of these emails ask the recipient to:
- Quickly arrange for a gift card purchase for an athletic recruit, or prospective student, or to cover a university expense
- Make an immediate wire transfer to an unfamiliar account
- Pay an online invoice
Typically the FROM address shows the name of a New York Tech manager, department chair, or dean, along with an unfamiliar email address. Sometimes the address itself is forged and looks like a real nyit.edu address. The SUBJECT may be a generic request for help (for example, "Quick Task,” “Are you available,” "Urgent request") or an invoice number. The body of the email may be something as simple as “Are you free? I’m heading into a meeting and cannot accept a phone call” or “Can you text me at xxx-xxx-xxxx” to something a little more descriptive such as “I need you to help me get iTunes gift cards from the store. I’ll reimburse you when I get back to the office.”
In all cases, the request is deemed as urgent and the intent is to make it appear that someone at New York Institute of Technology in a position of authority is directing you to complete a university or personal task via email. By responding, you risk theft, malware, and account compromise.
Email Phishing Scams
New York Institute of Technology’s IT department estimates it catches 150 virus emails and 20,000 spam messages daily. Even so, phishing emails (social engineering attacks to dupe you out of personal information) often make their way into nyit.edu email inboxes. Phishing “bait” can come in the form of instant messages, false ads on web pages, and other forms of electronic communication. The following information can help guard you against potential attacks.
How do Scammers Get Our Names and Email Addresses?
New York Institute of Technology publishes contact information on many college, school, department, and unit websites. Scammers can easily find organizational web pages with contact addresses, publicly-visible email groups that contain names and email addresses, and postings on social networks with names and addresses. They then set up free email accounts using those names and send to the groups they found online.
What You Can Do
- Be suspicious of communications with urgent, unfamiliar requests. Review the sending email address closely to see whether it is a nyit.edu address. Always check with the apparent sender by phone call, chat, or in-person if you are at all unsure of an email. Do not reply to the request itself.
- Ignore any request for payment via gift card. "Anyone who demands payment by gift card is always, always, always a scammer," according to the Federal Trade Commission (FTC). "Gift cards are for gifts, not payments."
- Verify unusual requests for money (via wire transfer, gift card, or other means) from your supervisor or leadership before acting.
- Don't open unexpected attachments or shared documents. Scammers frequently send emails that appear to be from someone you know to trick you into an action that will lead to infecting your computer with malware.
- Report emails impersonating people at New York Tech by sending them to infosec@nyit.edu. Send the email as an attachment vs. forwarding if possible.
- Report compromise. If you suspect you fell for a scam or your account was compromised, change your password immediately and contact the ITS Help Desk at nyit.edu/itshelp or via phone at 516.686.1188.
- And remember: We will NEVER ask you to reset your password via a link sent in an email.
Other Ways to Combat Online Theft of Information
- If an email from a company contains misspellings, it usually is a scam: delete it.
- Never give out personal, financial, or other sensitive information to just anyone who requests it.
- Be suspicious of email that requests sensitive information
- Never click on links embedded in an email that seems to come from a bank, financial institution or e-commerce vendor.
- Do not fill in forms attached to an email that ask for sensitive information.
- Never give out bank or account information without checking with the financial institution or at least ensuring that all URLs start with HTTPS.
- When in doubt, check! If you doubt the authenticity of a message, check directly with the institution.
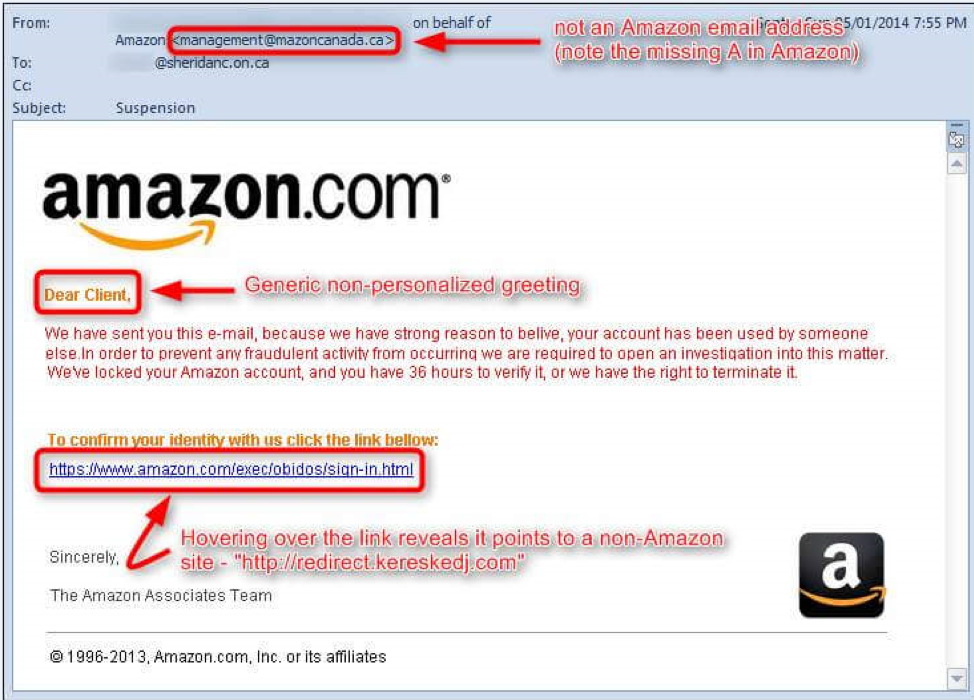
- At first glance, this email looks fine but take a closer look--don’t be duped:
Common Phishing Tactics
- Email Spoofing: The forgery of an email name/address so that the message appears to have originated from someone or somewhere other than the actual source. Email spoofing is a popular tactic used in phishing and spam campaigns because people are more likely to open an email when they think it has been sent by a legitimate or familiar source. The goal of email spoofing is to get recipients to open and/or respond to an urgent request. Do not respond to unusual requests. Always contact the person the email is allegedly coming from via phone or in person if you are unsure.
- Spear Phishing: A type of email spoofing that targets a specific individual. Spear phishing messages appear to come from a trusted source within the recipient’s own organization - generally, someone in a position of authority -- or from someone the recipient knows personally. Even if the sender appears to know you, never provide account information/passwords via email. Also, do not reply to the message; instead forward the message to a known email address of the person you think the message is coming from (e.g., an nyit.edu email address).
- Pharming Phish: A hijacked website domain name redirects you to an impostor site to steal information or online payments. “SECURE” or “HTTPS” in the web address box and/or browser indicates protected sites.
- Google Docs/ Dropbox Phishing: Web page(s) that mimic these sites and request your login credentials. By enabling a 2-step verification for these services, you can avoid this type of scam.
- Tech Support Scams: A “technical support” email requesting you to click on a link to enter your login information to avoid an interruption of service. Tech support members always request to talk with you before asking for access to your system.
- Infected Attachments: It’s simple—NEVER, EVER, EVER—we really mean NEVER—click on an attachment with an .exe extension or any attachment from someone you do not know.
ITS Help Desk will continue to update this web page offering information about common phishing tactics and best practices to avoid these scams. For more information, or to report any suspicious activity, please contact the ITS Help Desk at nyit.edu/itshelp or call us at 516.686.1188.
For More Information, Refer to these Resources:
- Phishing Scheme Targets Professors’ Desire to Please Their Deans — All for $500 in Gift Cards. (Chronicle of Higher Ed, 1/23/2019)
- Beware of Growing Scam Involving Gift Cards. (CBS, 12/26/18)
- Scammers Increasingly Demand Payment by Gift Card. (FTC, 10/16/18)
- SCAM OF THE WEEK: "The Boss Needs iTunes Gift Cards for Customers... NOW." (KnowBe4 Security Awareness Training Blog, 9/12/18)
- Asked to Pay by Gift Card? Don’t. (FTC, 5/31/18)